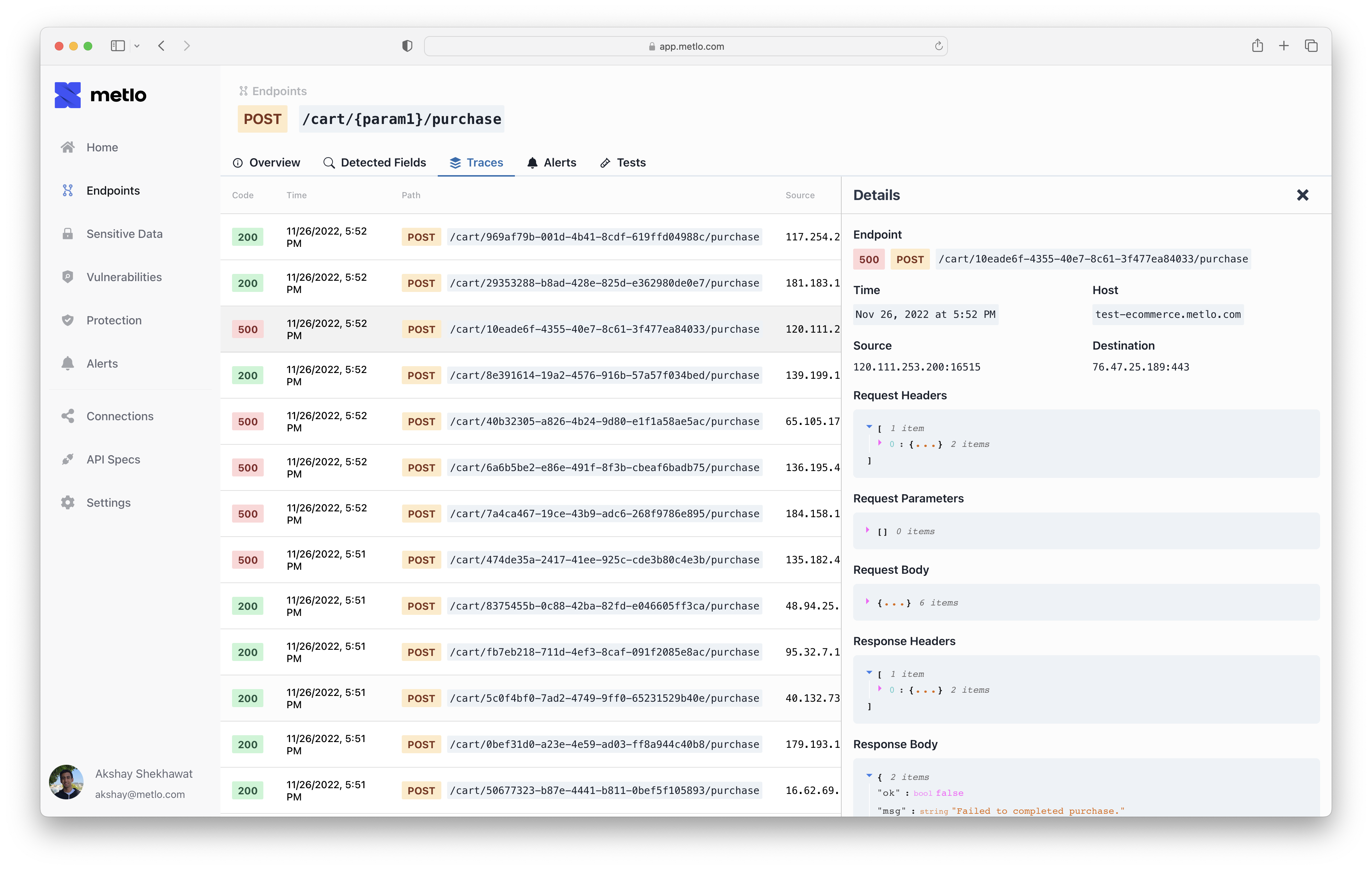
Endpoint Overview
The endpoints page shows an overview of your endpoints and hosts. By default they are sorted “riskiest” first, where the endpoints with the most sensitive data are the riskiest endpoints. You can filter this list by:- Host
- Risk Score
- Sensitive Data Classes
- Authenticated/Unauthenticated
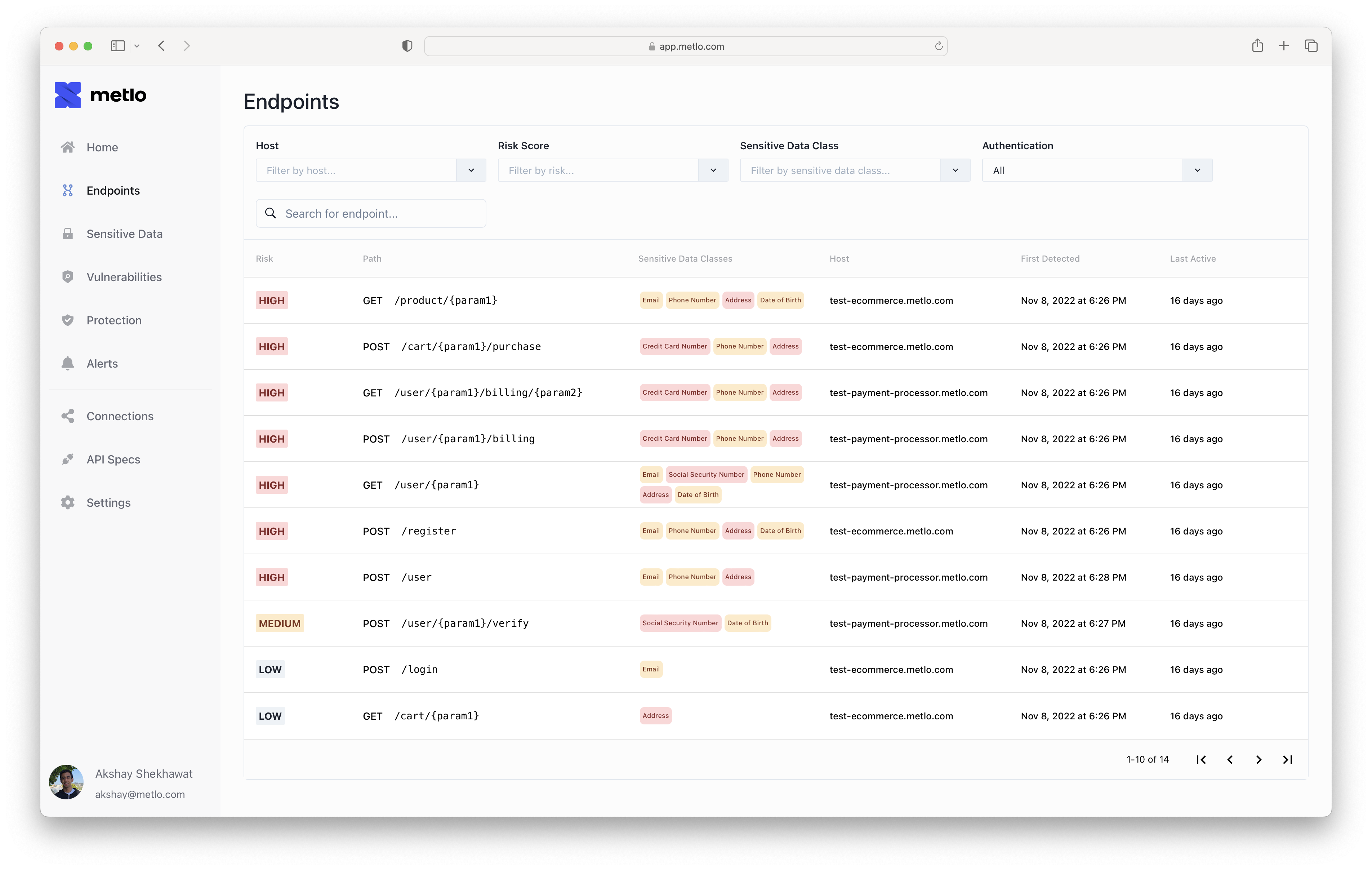
Endpoint Details
Each endpoint has a detail view where you can dig deeper into its characteristics. This page shows you the following details:- Number of PII Fields
- Usage history
- The last time this endpoint was used
- Authenticated/Unauthenticated
- Risk Score
- Generated Open API Spec
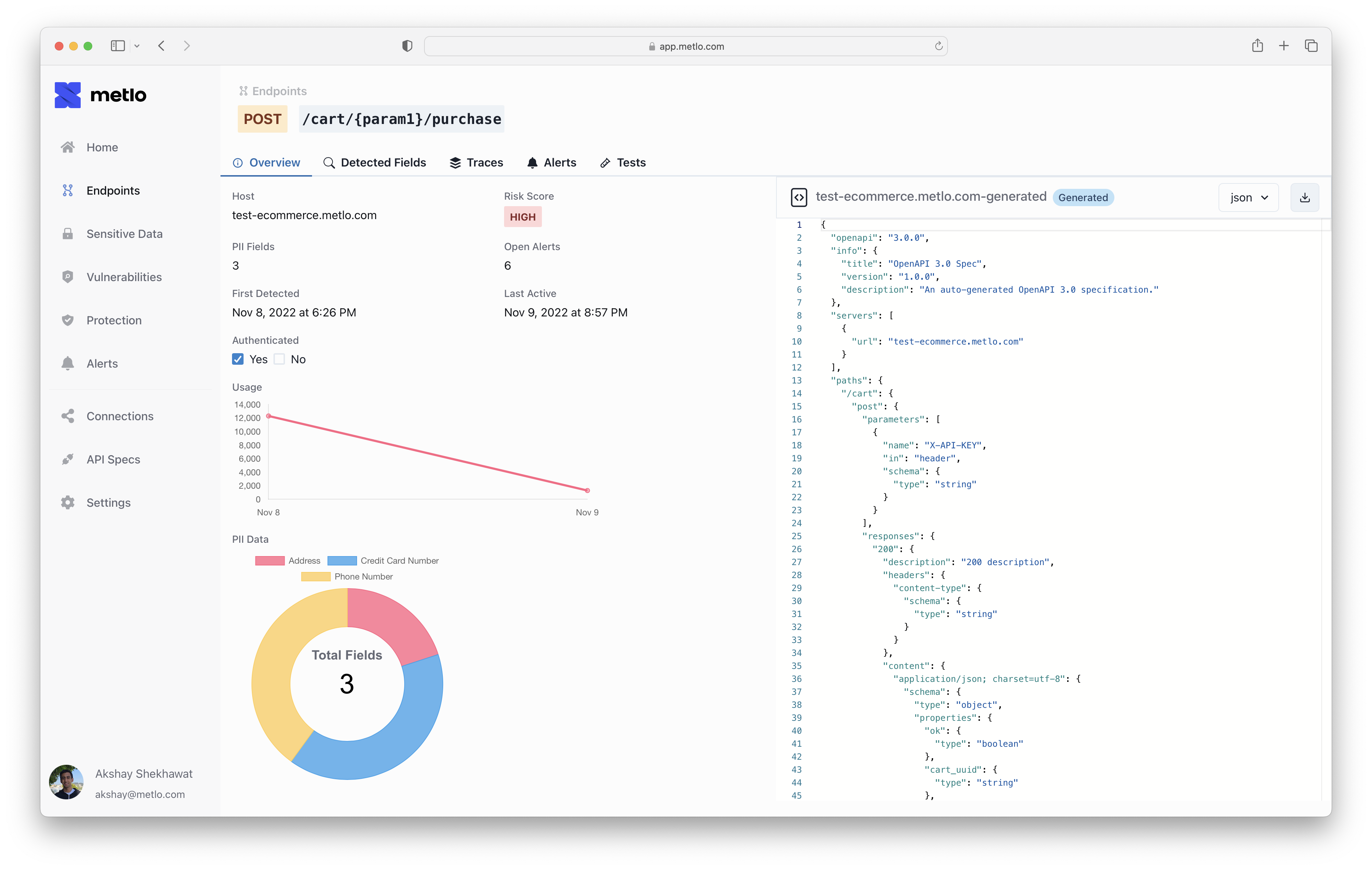
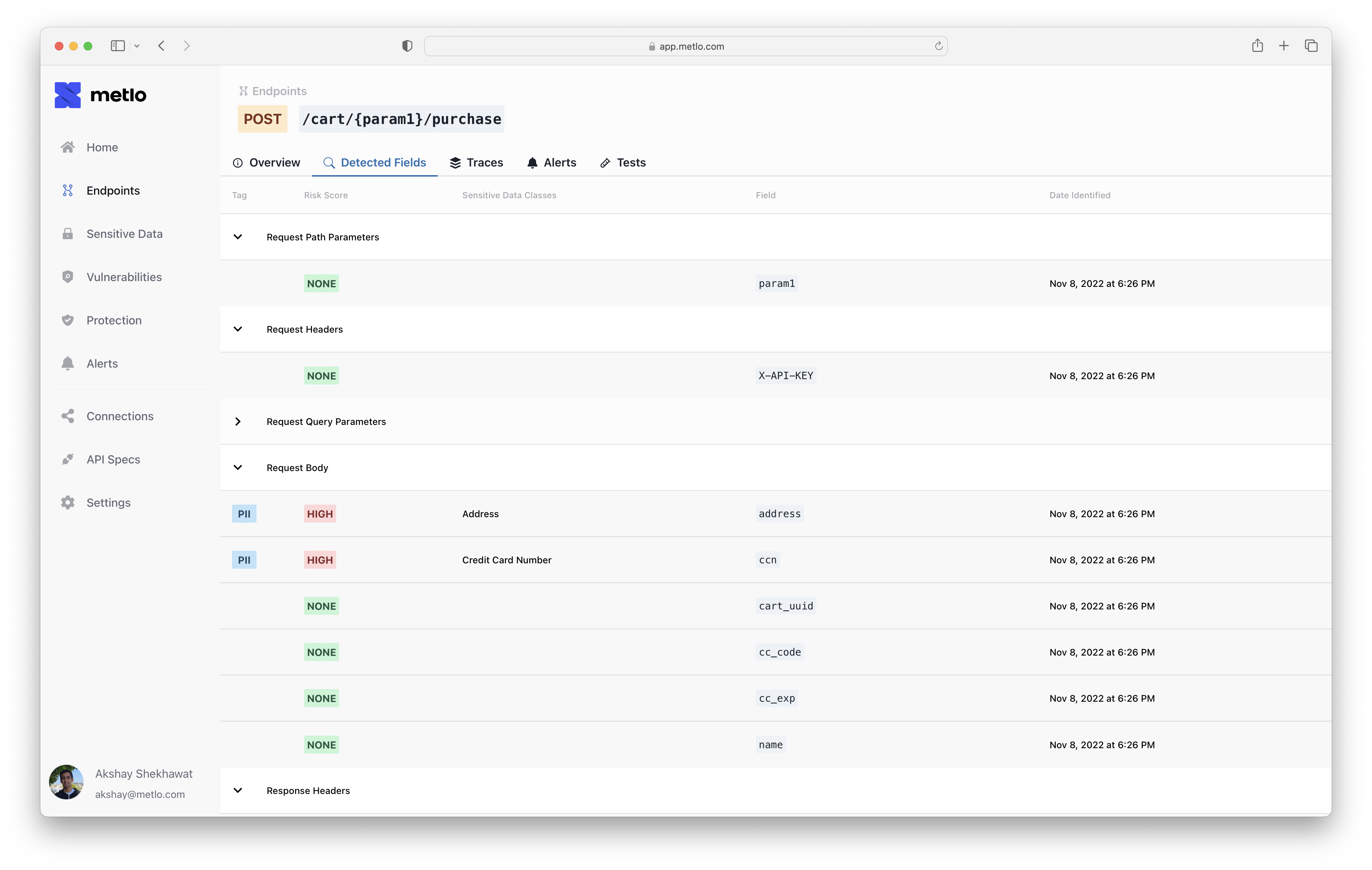
Traces
If you’re investigating an issue, Metlo stores traces so you can dig into what traffic your endpoint is receiving. Traces more than an hour old are automatically deleted.